Cryptography¶
To ensure security, the Waves Enterprise platform uses cryptographically resistant algorithms complying with GOST requirements, as well as qualified electronic signatures.
The platform provides a choice of cryptography to be used based on one of the standards:
GOST-cryptography - for implementation of projects in government structures and departments;
Elliptical curve Curve25519 - for projects which do not require strict compliance with GOST (commercial companies, organizations outside the Russian Federation).
Data Pre-processing¶
All byte sequences before hashing or signing operations are converted using Base58 or Base64 algorithm.
Hint
Base64 is a binary data encoding standard using 64 ASCII characters. The encoding alphabet contains Latin symbols and numbers A-Z, a-z and 0-9 (62 characters) and 2 service symbols. Every 3 source bytes are encoded with 4 characters (¹ ⁄ ₃ magnification).
Hint
BASE58 is a variant of encoding binary data in the form of alphanumeric text based on the Latin alphabet. It contains 58 characters, the characters used in Base64, such as 0, O, I, L, +,/ are excluded. It is used for data transmission in heterogeneous networks (transport coding).
GOST-Cryptography¶
Hashing algorithm is implemented according to GOST R 34.11 2012 ‘Information Technology. Cryptographic Protection of Information. Hashing Function’. The Stribog function is used with 256 bits output blocks.
The encryption algorithm is implemented according to GOST ‘Information processing systems. Cryptographic protection. Algorithm of cryptographic transformation’.
EDS generation and verification algorithms are implemented according to GOST R 34.10-2012 ‘Information Technology. Cryptographic Protection of Information. Electronic Digital Signature Generation and Verification Processes’. The key length is 256 bits.
Using an elliptical curve Curve25519 (Waves cryptography)¶
The hashing algorithm is implemented by successive hashing functions Blake2b256 and Keccak256. The size of output blocks is 256 bits.
EDS generation and verification algorithms are implemented on the basis of elliptical curve Curve25519 (ED25519 with X25519 keys). The key length is 256 bits.
Encrypting text data in transactions¶
The Waves Enterprise platform allows to encrypt/decrypt the text data using the session keys. The option is used to encrypt any kind of text information, for example, Docker contract parameters or data from Data Transactions.Encryption of text data can be performed both individually for each recipient, with forming of a unique instance of the encrypted text, or with forming of a single encrypted text for a group of recipients. Limit size to encrypt data is 165 Kbytes. Hashing algorithms correspond to the chosen cryptography scheme (GOST or Waves).
Encryption algorithm¶
Symmetric CEK and KEK keys are used to encrypt/decrypt data. CEK (Content Encryption Key) is the key for the encrypting text data, KEK (Key Encryption Key) is the key for encrypting the CEK. The CEK key is generated by a node randomly using the appropriate hashing algorithms. The KEK key is generated by a node based on Diffie-Hellman algorithm, using public and private keys of sender and recipients, and is used to encrypt the CEK key.
The symmetric CEK key is unreachable and does not appear in the encryption process. It is transmitted from the sender to the recipient in the encrypted form (wrappedKey) via open communication channels along with the encrypted message. One of such channels can be a record to the blockchain — a DataTransaction or a smart contract state. The KEK key does not transmit from the sender to recipients, it is restored by the recipient based on its private key and the known public key of the sender (Diffie-Hellman key exchange algorithm).
Text data encryption/decryption is performed using the crypto method. This method allows to encrypt the text individually for each recipient or for all recipients together.
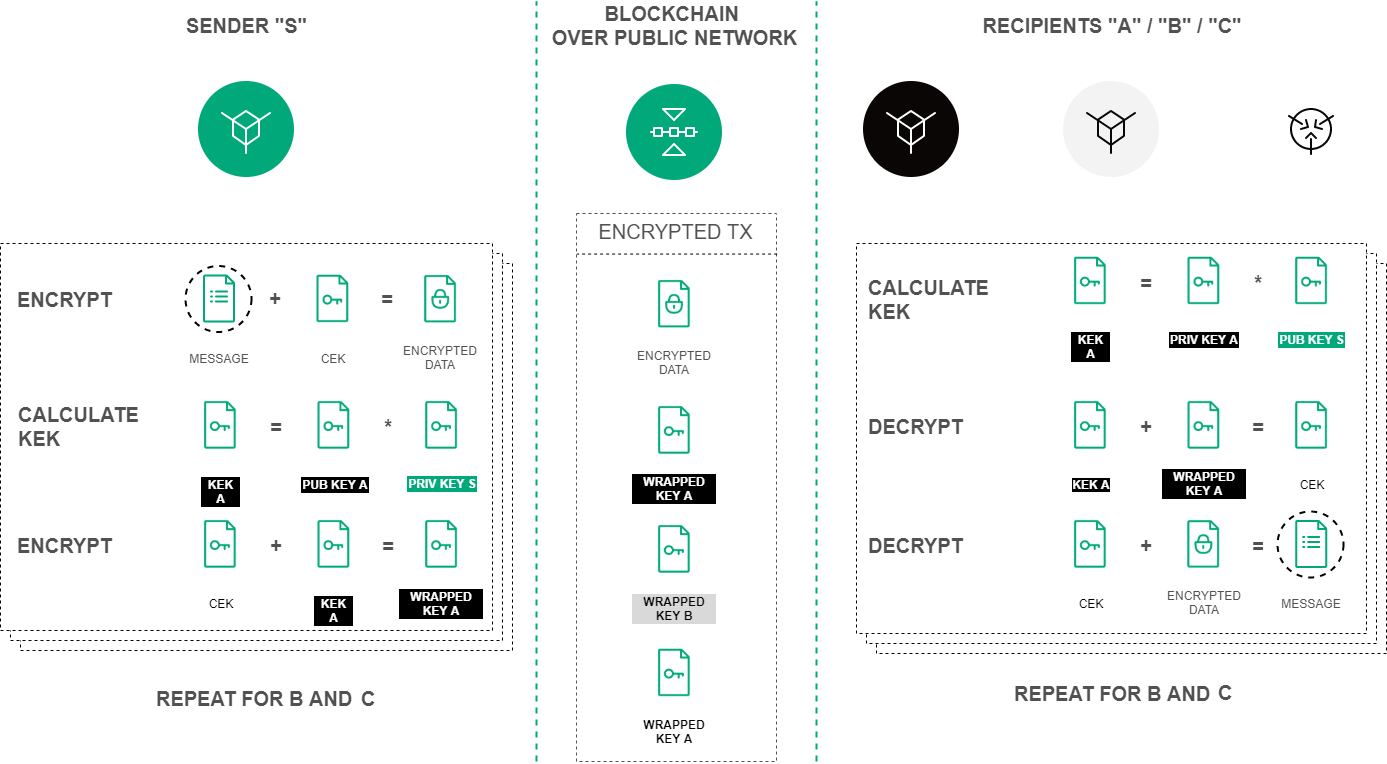
Encryption procedure of the text data based on the Diffie-Hellman algorithm¶
Encryption/decryption process includes the following actions:
Use the POST /crypto/encryptSeparate method to encrypt data for each recipient separately. Specify the following parameters inside the JSON request:
sender- the sender address.password- a key pair password of the sender, which is generated at the same time as the account itself.encryptionText- the text for the encryption.recipientsPublicKeys- an array with recipients public keys list inside.
Use the POST /crypto/encryptCommon method to encrypt data for all recipients with a single CEK key. Specify the same parameters as inside the POST /crypto/encryptSeparate method into the JSON request.
Use the POST /crypto/decrypt method for the decryption. Specify the following parameters inside the JSON request:
recipient- the recipient address.password- a key pair password of the recipient, which is generated at the same time as the account itself.encryptedText- the encrypted text data.wrappedKey- the wrapped key obtained by encoding the data.senderPublicKey- the sender public key.