Data Privacy¶
Blockchain platform Waves Enterprise provides the confidential data transfer and storage between the participants of network interaction. Protection of confidential data during its transfer and storage is provided by a set of groups, which contain a list of participants for the interaction with private data.
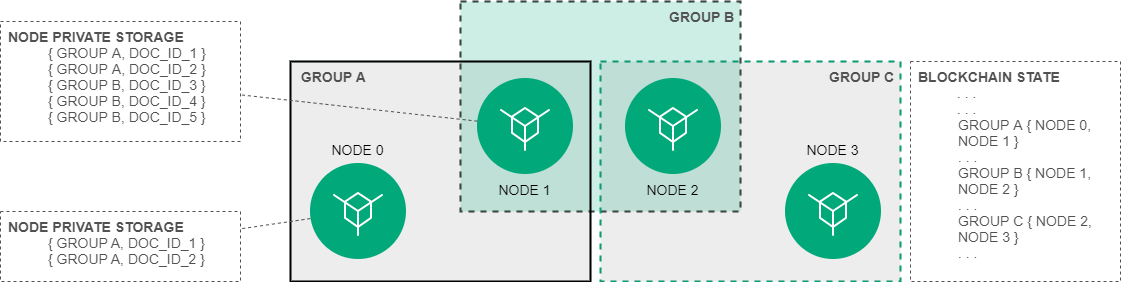
Access groups¶
Usually the access group is created by the net participants who need to arrange the private data exchange. Any participant can create an access group and add into it any number of other participants. Only nodes can exchange information within a group.
The group contains the following parameters:
name (policyName);
description (Description);
the list of confidential data recipients (Recipients);
the list of the policy owners with editing rights (Owners).
The access group is created by sending transaction CreatePolicy (type = 112, group creation) into the blockchain.
Owners can change the access group. To make this it is necessary to send the UpdatePolicy (type = 113, group editing) transaction into the blockchain.
For external access and getting the information about groups there are using specified API Node requests: GET /privacy/{policy}/recipients, GET /privacy/{policy}/getHashes, GET /privacy/getInfo/{hash}.
Sending and receiving the data¶
The data is sending via POST /privacy/sendData request through its own node of the organization, which checks the sender’s belonging to the specified group. If the check is successful, the data is written to the node store, and the PolicyDataHash (type = 114, sending the data hash) transaction is initiated with the calculated hash sum of the data. The size of the transferred data to the network is up to 20 MB.
When receiving a transaction with the hash sum from the transmitted data, the receiving party checks whether the blockchain node is involved in the group specified in the transaction. If the participant is belong to the group, the getPrivateData request for confidential data is executed. The request is executed at the network address of the group participant via P2P connection. To ensure the security of data transmission over an unprotected communication channel, a set of encryption algorithms on a symmetric key and the creation of session keys, as well as the Diffey-Hellman protocol are used.