Authorization service¶
The authorization service is an external service that provides authorization for all components of the blockchain network. This service is built using the OAuth 2.0 authorization protocol. OAuth 2.0 is an open framework for realization of the authorization mechanism, allowing third parties limited access to protected resources without transferring credentials to the third party. The data flow scheme between participants sharing information using OAuth 2.0 is presented below.
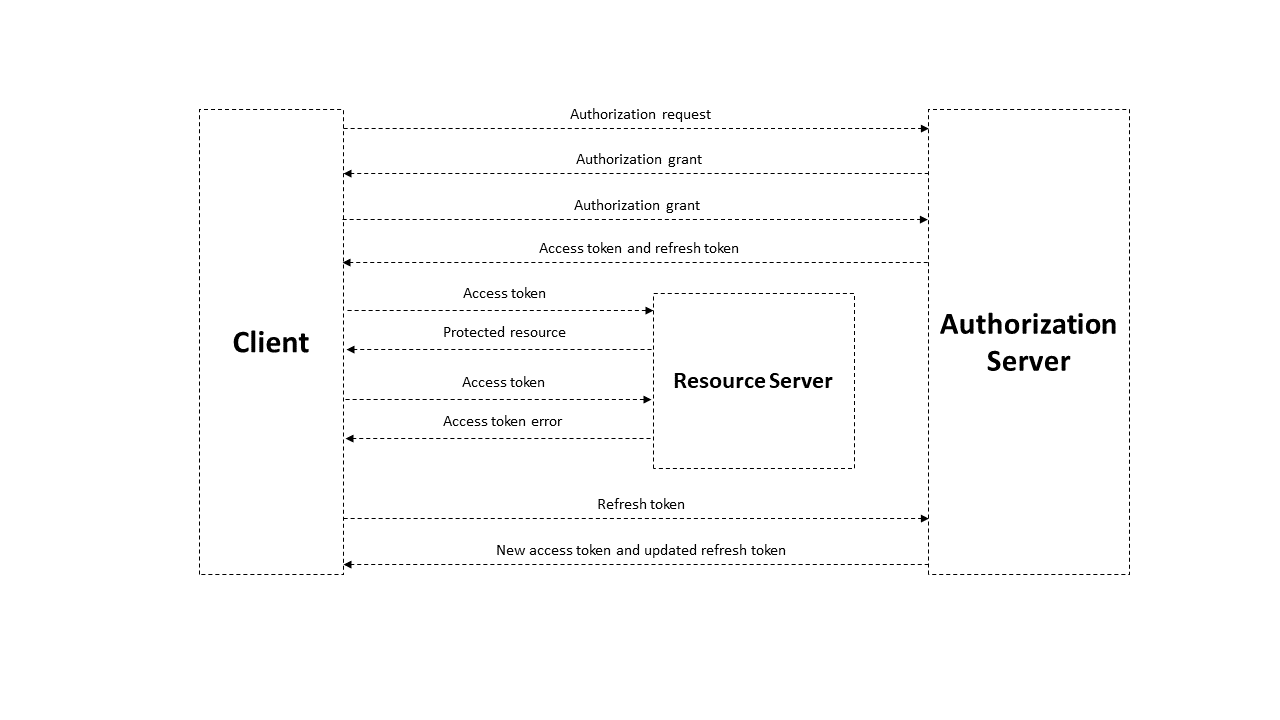
Basic authorization scheme based on OAuth 2.0 protocol¶
A JSON Web Token is used to authorize each request from the client to the server and has a limited lifetime. The client can receive two types of tokens: access and refresh. The access token is used to authorize requests for access to protected resources and to store additional information about the user. The refresh token is used to obtain a new access token and to refresh the refresh token.
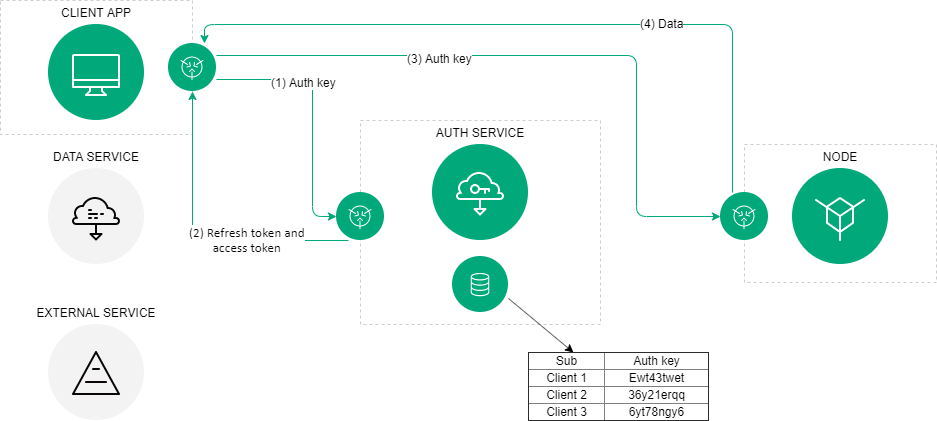
The authorization scheme of the Waves Enterprise blockchain platform¶
In general, the authorization scheme includes the following operations:
The client (which could be any blockchain network component like the web client, data service, or an external application) provides its authentication data to the authorization service once.
If the initial authentication procedure is successful, the authorization service stores the client’s authentication data in the database, generates and sends signed access, and refresh tokens to the client. Tokens include the lifetime info and basic customer data, such as an ID and a role. Client authentication data is stored in the authorization service configuration file. The client checks the lifetime of the access token each time before sending a request to a third-party service. In case the token is expired, the client refers to the authorization service to obtain a new access token. The refresh token is used for requests to the authorization service.
The client sends a request to receive data from a third-party service using the current access token.
The external application checks the lifetime of the access token and its integrity, then compares the previously obtained public key of the authorization service with the key contained in the signature of the access token. If the token is successfully verified, the service provides the requested data to the client.