Data encryption operations¶
Symmetric CEK and KEK keys are used to encrypt/decrypt data. CEK (Content Encryption Key) is the key for the encrypting text data, KEK (Key Encryption Key) is the key for encrypting the CEK. The CEK key is generated by a node randomly using the appropriate hashing algorithms. The KEK key is generated by a node based on Diffie-Hellman algorithm, using public and private keys of sender and recipients, and is used to encrypt the CEK key.
The symmetric CEK key is unreachable and does not appear in the encryption process. It is transmitted from the sender to the recipient in the encrypted form (wrappedKey) via open communication channels along with the encrypted message. One of such channels can be a record to the blockchain — a DataTransaction or a smart contract state. The KEK key does not transmit from the sender to recipients, it is restored by the recipient based on its private key and the known public key of the sender (Diffie-Hellman key exchange algorithm).
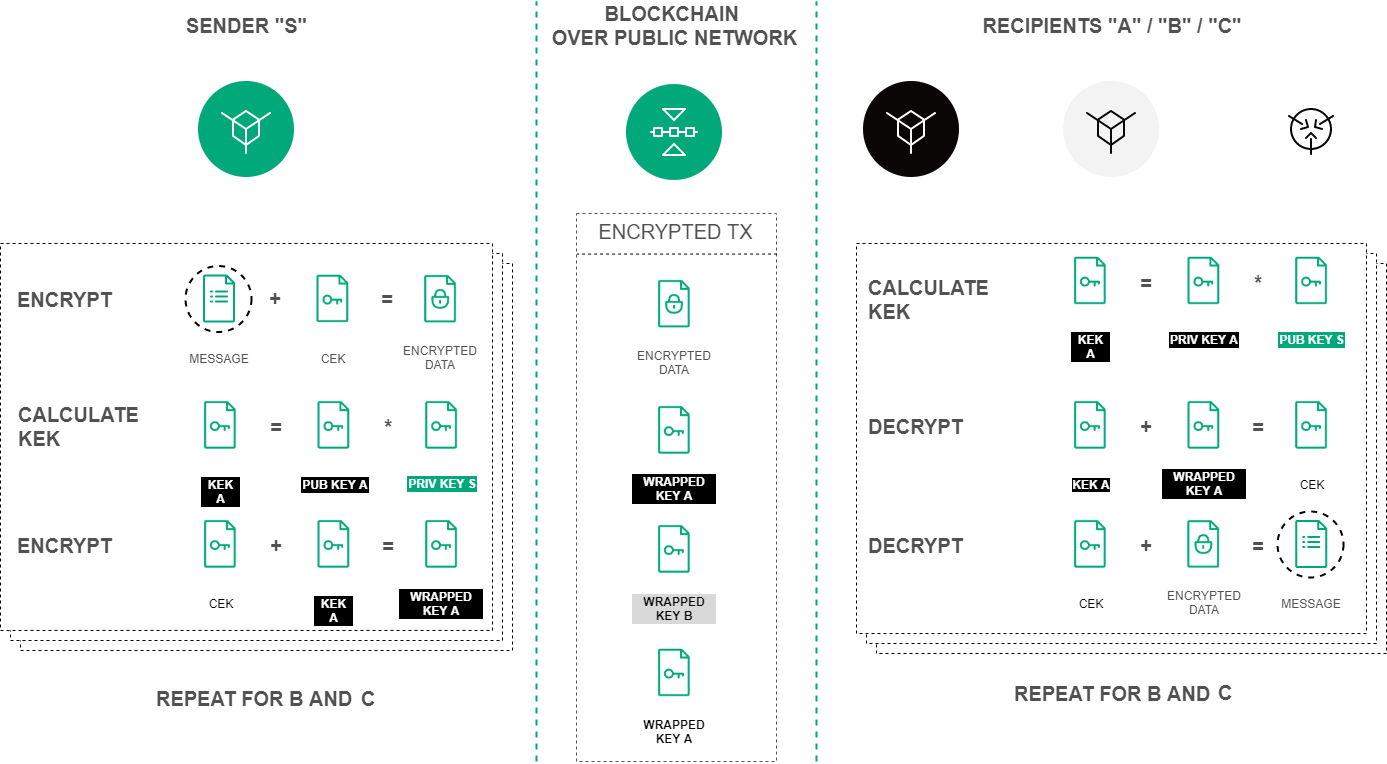
Encryption procedure of the text data based on the Diffie-Hellman algorithm¶
Encryption/decryption process includes the following actions:
Use the POST /crypto/encryptSeparate method to encrypt data for each recipient separately. Parameters in the request object:
sender- the sender address;password- a key pair password of the sender, which is generated at the same time as the account itself;encryptionText- the text for the encryption;recipientsPublicKeys- an array with recipients public keys list inside.
Use the POST /crypto/encryptCommon method to encrypt data for all recipients with a single CEK key.
Use the POST /crypto/decrypt method for the decryption. Parameters in the request object:
recipient- the recipient address.password- a key pair password of the recipient, which is generated at the same time as the account itself.encryptedText- the encrypted text data.wrappedKey- the wrapped key obtained by encoding the data.senderPublicKey- the sender public key.