Role model¶
The blockchain platform implements a mechanism limiting actions of participants based on the role model which allows the platform owner to protect participants from threats, such as:
attacks of unscrupulous miners on blockchain network;
unauthorized issue of tokens;
unauthorized access to confidential information;
other illegal actions of intruders.
The procedure for issuing and revoking permissions is given in module Role management.
Roles list¶
The following table provides a list of possible platform roles:
Role name |
Authority |
|---|---|
permissioner |
Add transactions to modify the permission list |
blacklister |
Add transactions to modify the black list |
miner |
Create new blocks |
issuer |
Add transactions for issuing, reissuing, and burning tokens |
dex |
Add the exchange transaction (deprecated) |
contract_developer |
Add the transaction to create a docker contract |
connection-manager |
Add the transaction for registering/deleting node in the blockchain network |
banned |
It is forbidden to send any transactions to the blockchain. |
Permission model¶
Permission model describes a mechanism for applying different types of permissions when validating operations in a blockchain.
Hint
The node with the permissioner role can assign to itself any existing role in the system.
Action |
Action permission condition |
|---|---|
Assign or remove a role |
Available permissioner role |
Add or Remove from blacklist |
Available blacklister role |
Registration of the new node to the net |
Available contract_developer role |
Generation and issue of blocks |
Available miner role |
Token operations (issue, reissue, burn) |
Available issuer role |
Token transfer (transfer, mass transfer) |
User not in the blacklist |
Token leasing (lease, lease cancel) |
User not in the blacklist |
Creating an alias (alias) |
User not in the blacklist |
Create a docker contract |
Available contract_developer role |
Execution of docker contract |
User not in the blacklist |
Update the permission list¶
A permission transaction is used to modify the permission list.
JSON description:
Transaction Type
Version
Sender PublicKey
Target Address or Alias
Timestamp
Operation Byte
Role Byte
Timestamp
Due Timestamp Defined Byte (0 - None, 1 - Defined)
Due Timestamp Bytes
The following diagram shows the sequence of actions when updating a permission list.
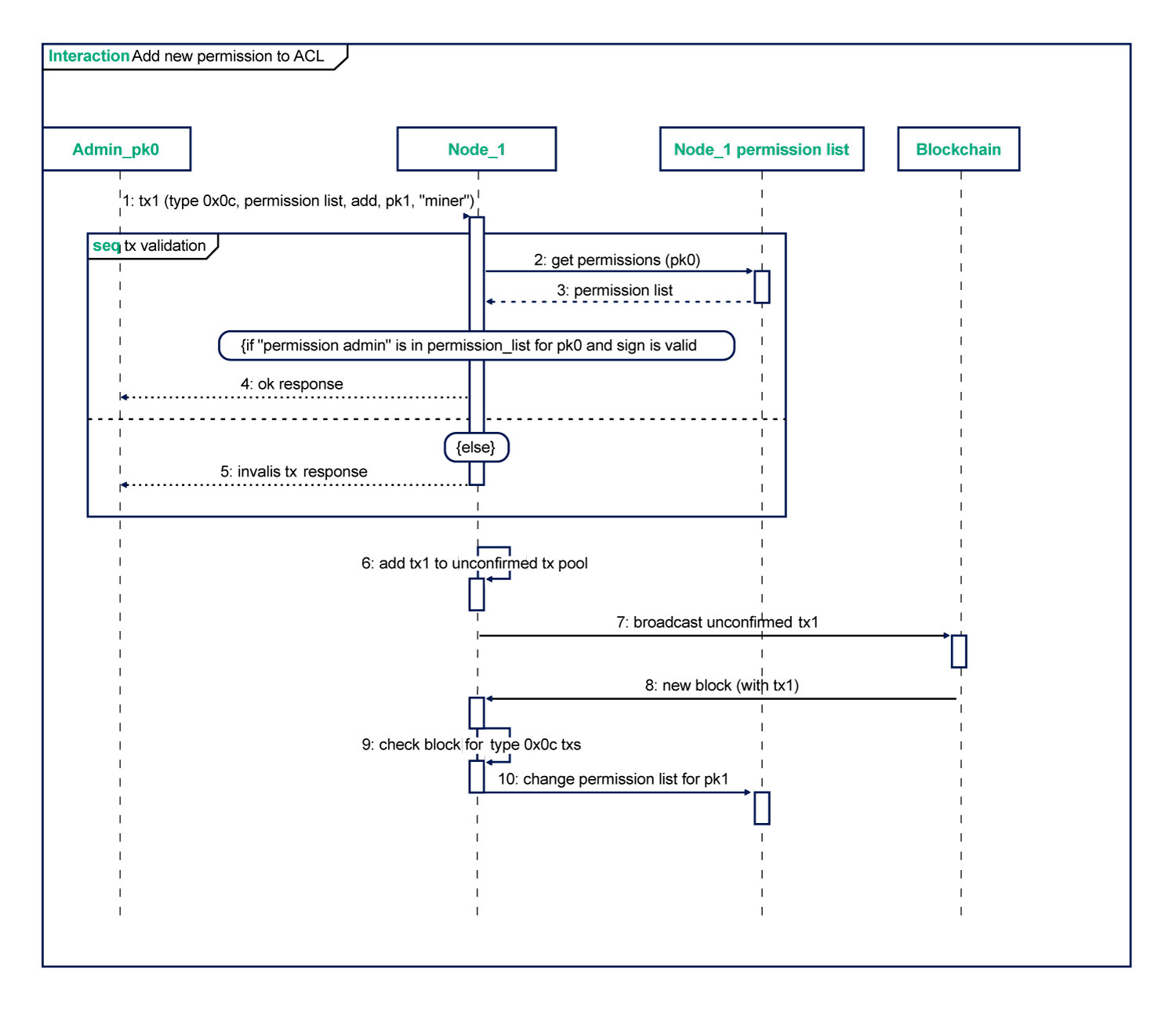
When modifying the permission list, the platform performs the following checks:
Sender is not in the blacklist.
Sender has the role of permissioner.
DueTimestamp (role duration) > Timestamp (current time).
This role is not active (if added) or active (if removed).